Covert Bear VPN
We've got you coveredLife without a VPN
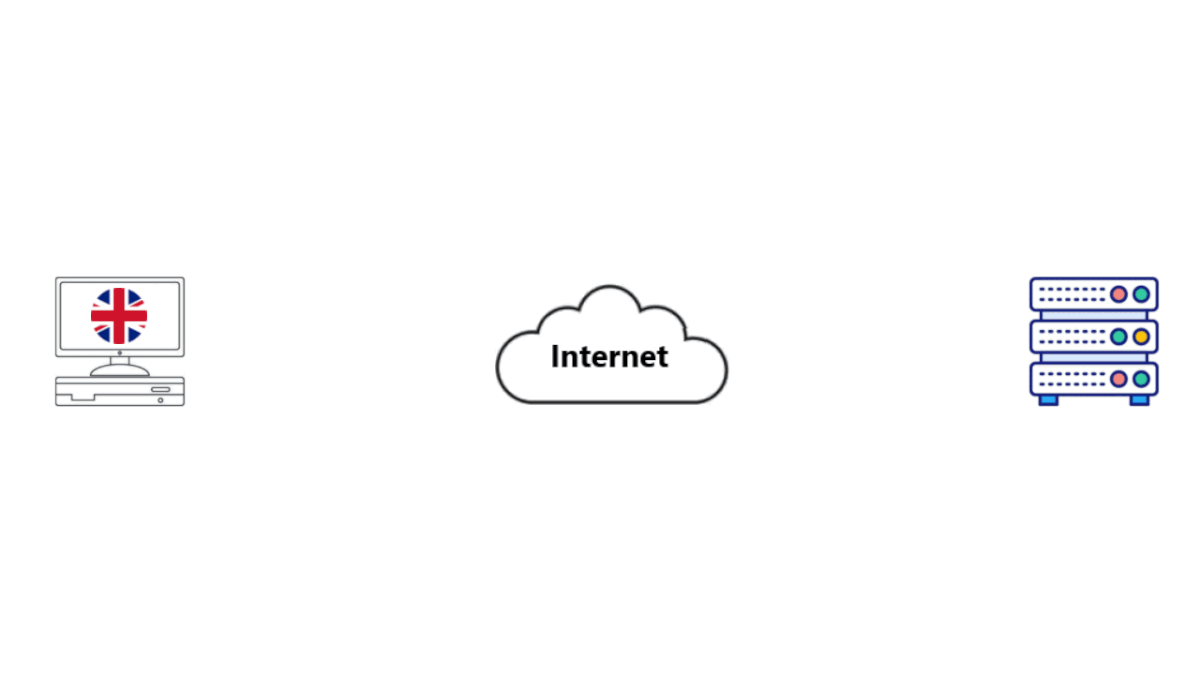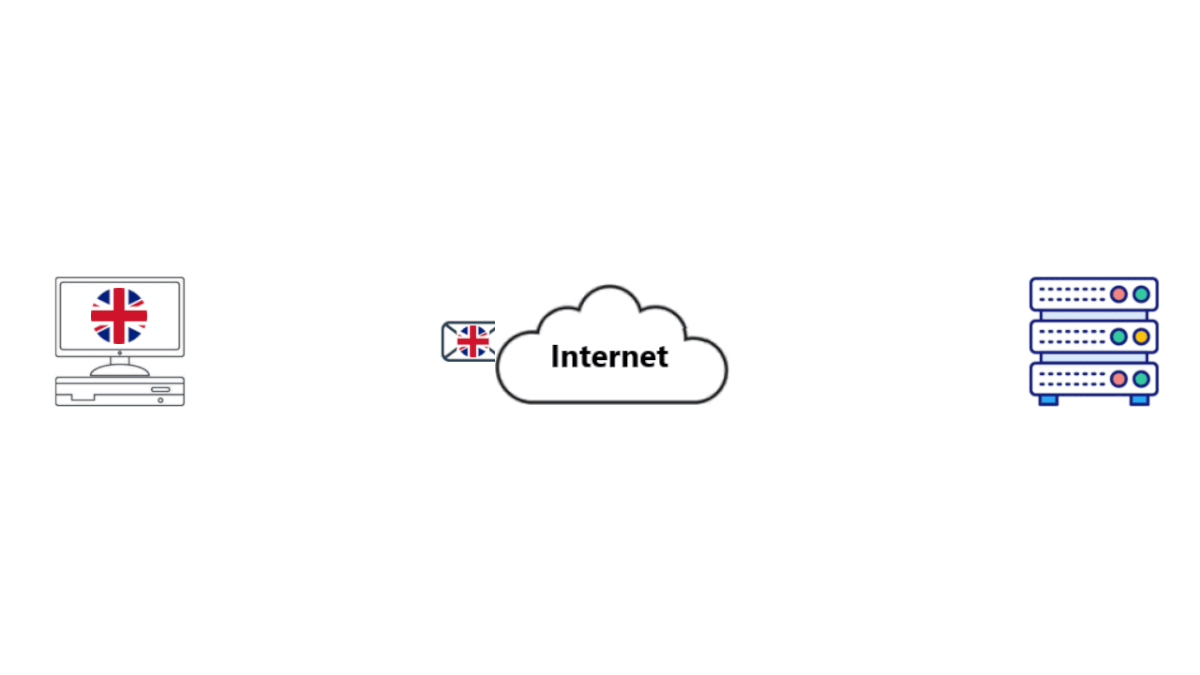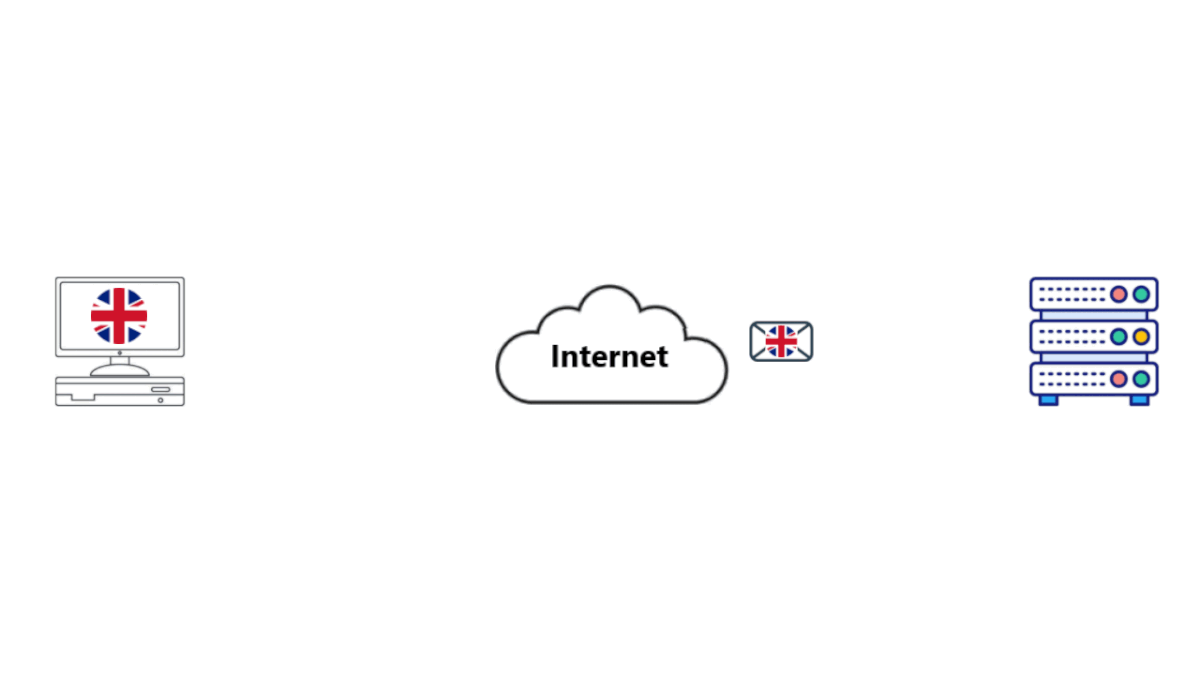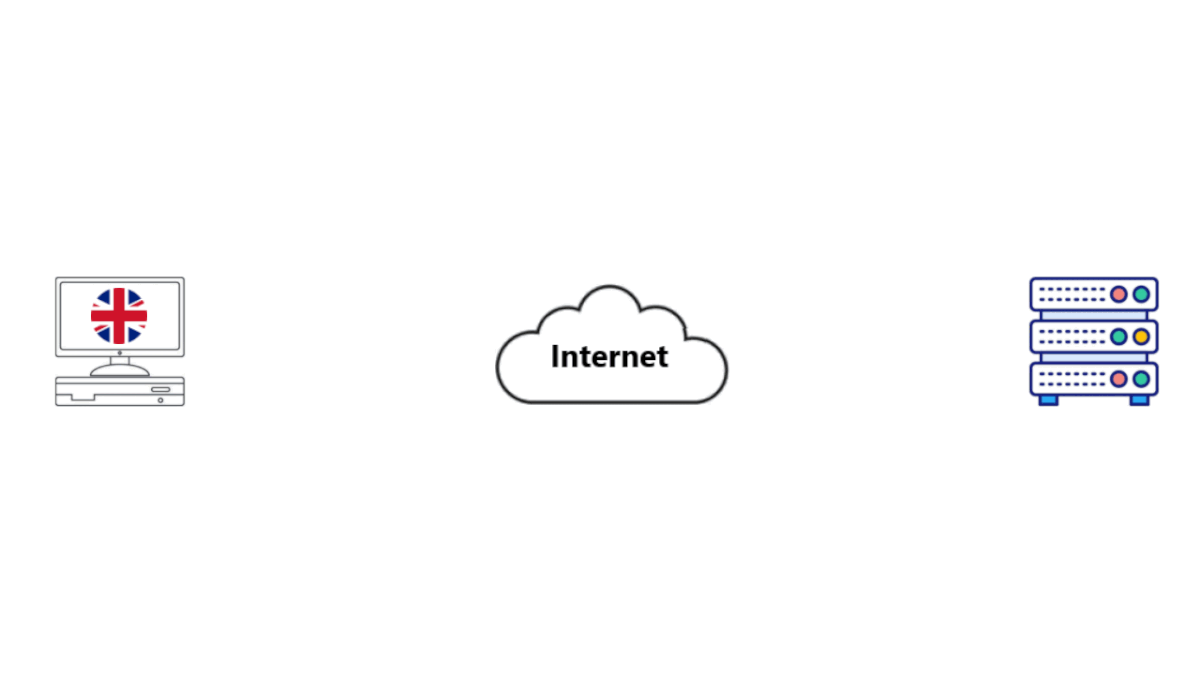 What happens when you use the internet?
What happens when you use the internet?• Be you, an internet user sitting on your computer in the UK.
• You type in "what is a VPN" on Google or some other Search Engine (SE) (SE), even ones like Duckduckgo, and hit Enter.
• Behind the scenes, your computer sends out an internet packet to Google (or other Search Engine [SE]) to get you search results. The packet goes through your modem-router and out to your Internet Service Provider (ISP).
•Your ISP notes down your IP address and sees that you are searching "what is a VPN". It passes on the packet from Router to Router until it reaches your desired SE.
• The SE notes down your IP address and what you are searching for. It gets the results and sends it back to you.
• Everytime you access the Internet in this way, you're exposed to the Government, your ISP, Hackers, and of course the Servers you access.
• Information is power, and all of these people want yours. A digital profile is being made with all of your likes and dislikes, this information is then sold so others can profit off of you! Throughout all of this, you are the one who loses.
• Everything you do online is being recorded, what you search for, what you watch, etc.
How does a VPN help?
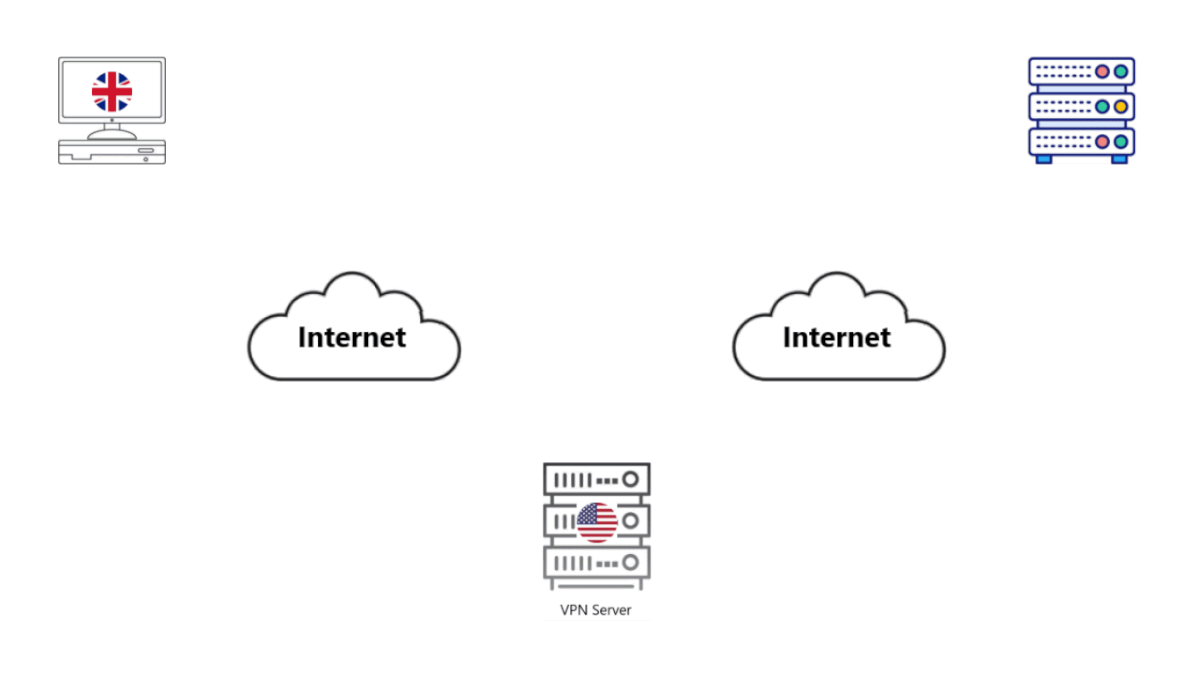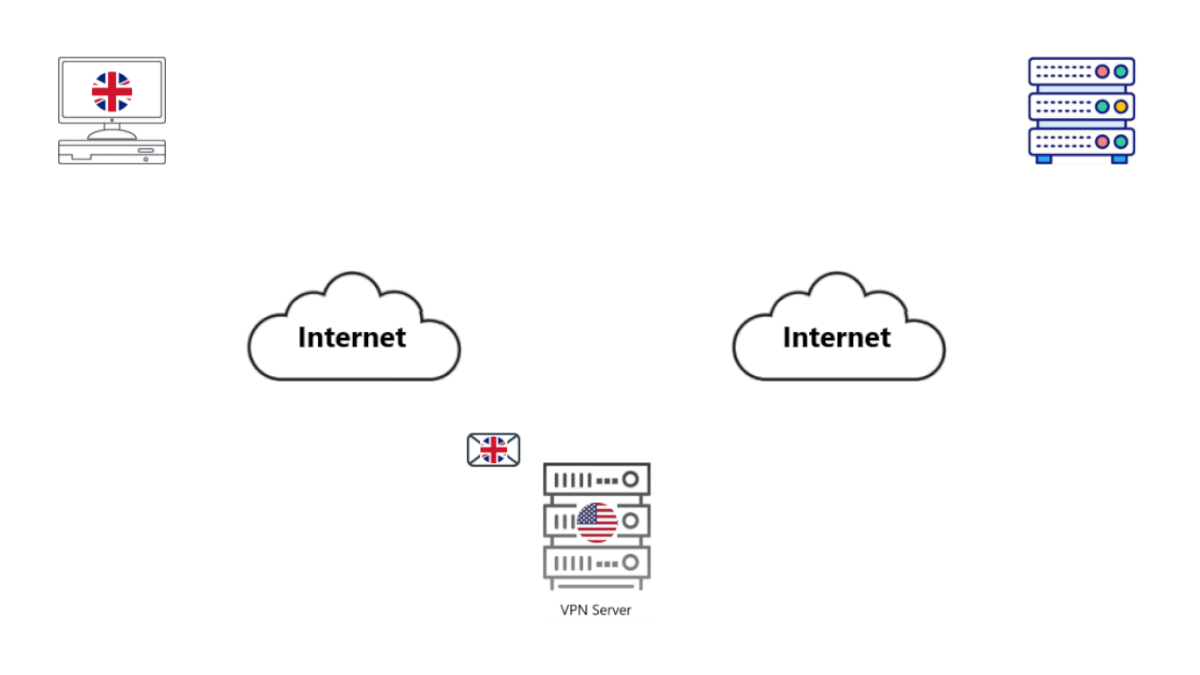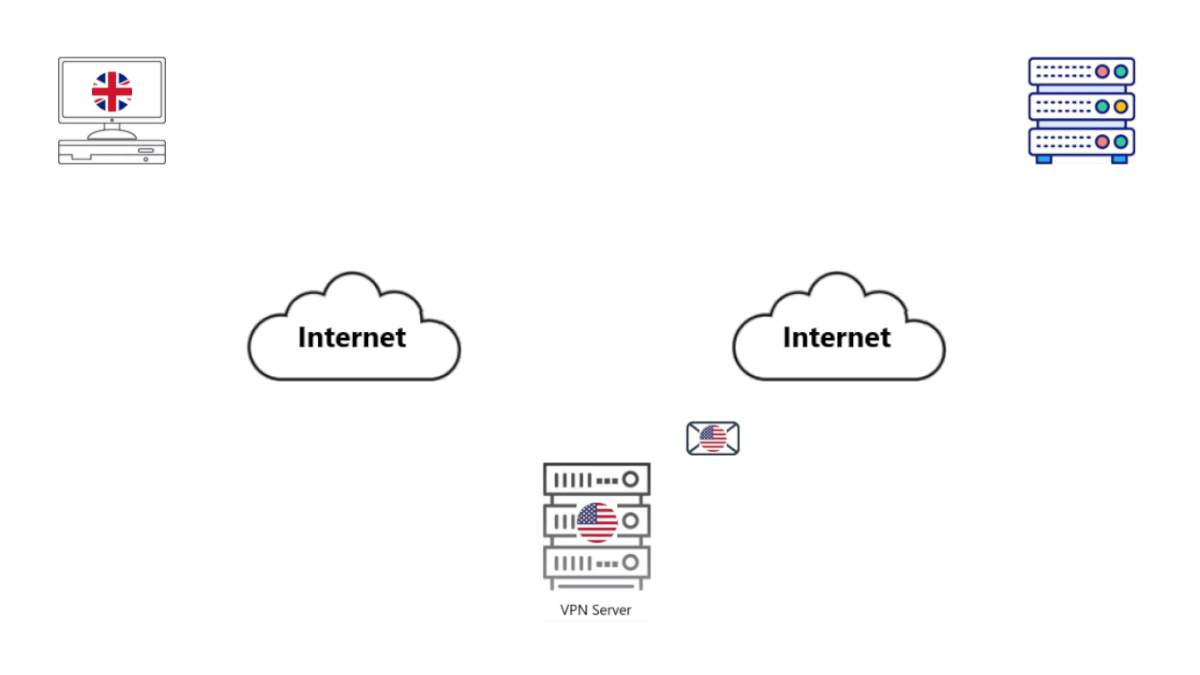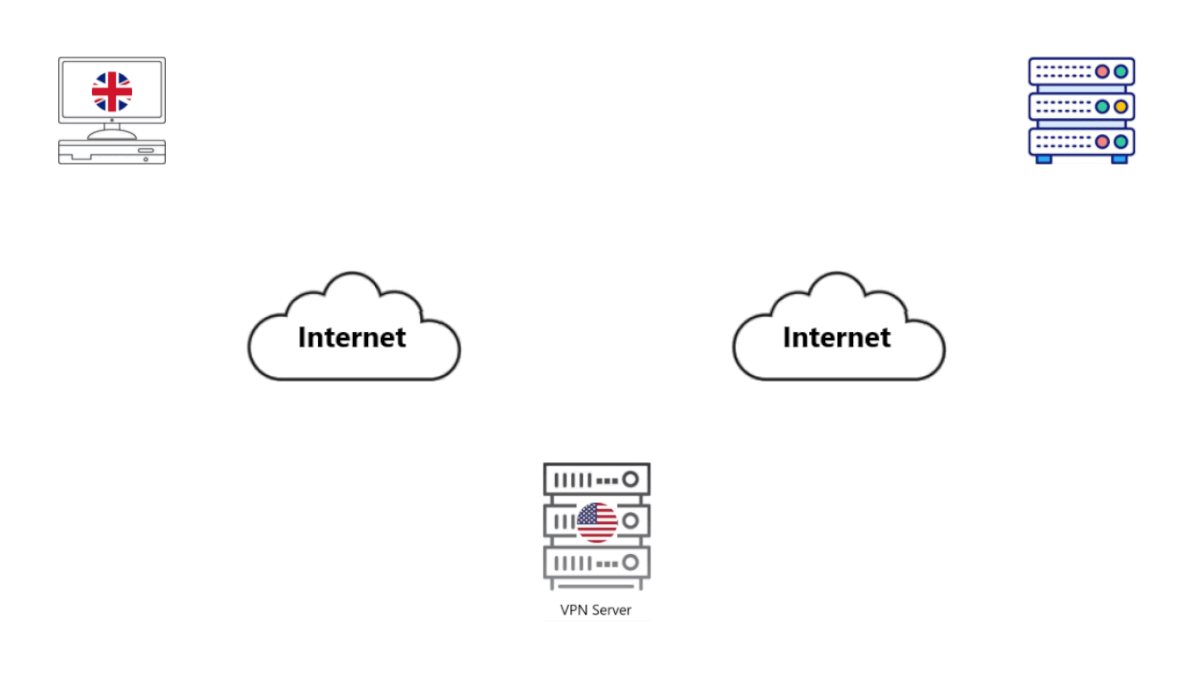 I get Covert Bear, now what?
I get Covert Bear, now what?
• First, pat yourself on the back. You've made the right choice.
• Be you, same internet user sitting on your computer in the UK.
• You type in "what is a VPN" on your Search Engine (SE) and hit Enter.
• Your computer sends an encrypted message to your VPN. It passes through your modem-router and out to your Internet Service Provider (ISP).
• Your ISP looks at the packet, nothing in it makes sense. It passes it on the packet from Router to Router until it reaches your VPN.
• Your VPN decrypts the message, then forwards the search query to the SE.
• The SE notes down the IP address of the VPN and what it believes the VPN is searching for.
• It gets the results and sends them back to the VPN.
• The VPN encrypts the packet and forwards it back to you. It's decrypted on your end.
• Checkmate Government, ISP, Hackers, and Servers you access.
• Note, in the image the VPN is located in the USA. Whenever you access the internet, it appears as if you are in the USA (or wherever your VPN is). Your Location is thus kept private.
Why don't I just get any VPN?
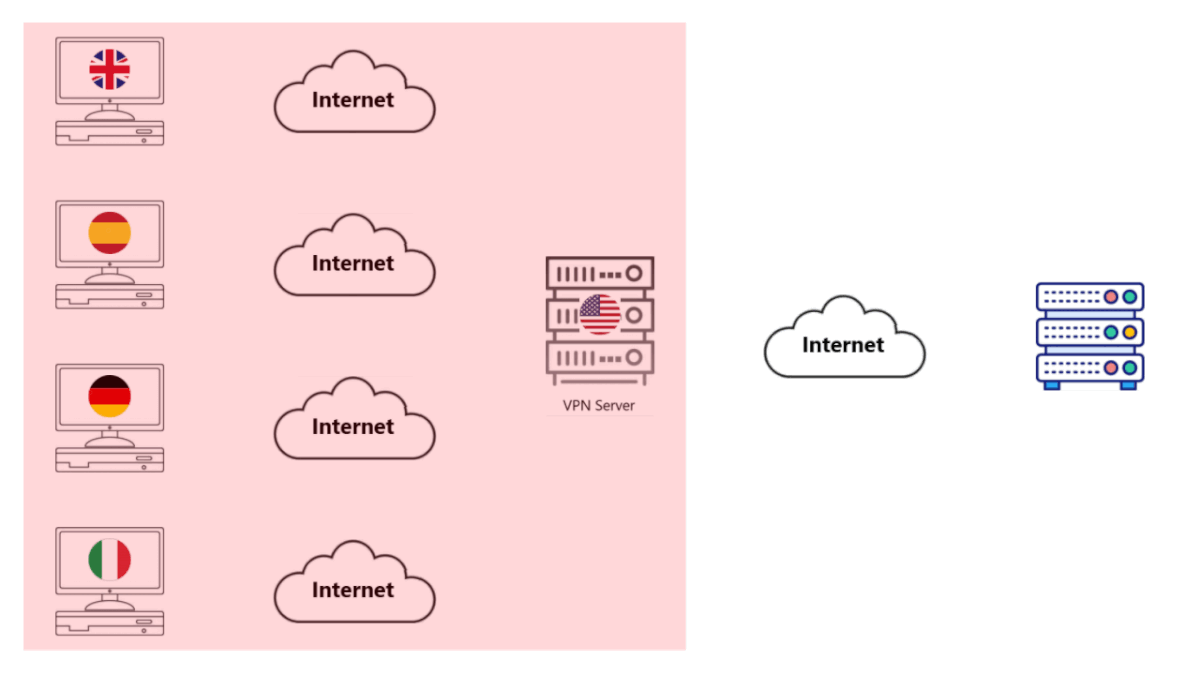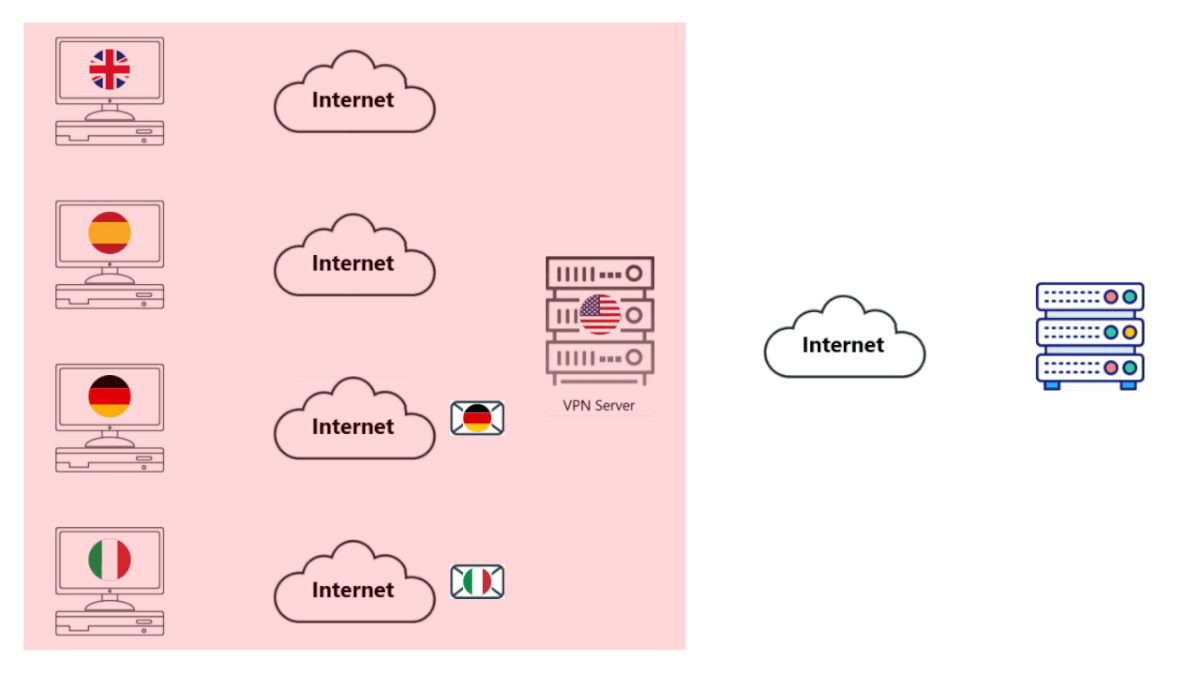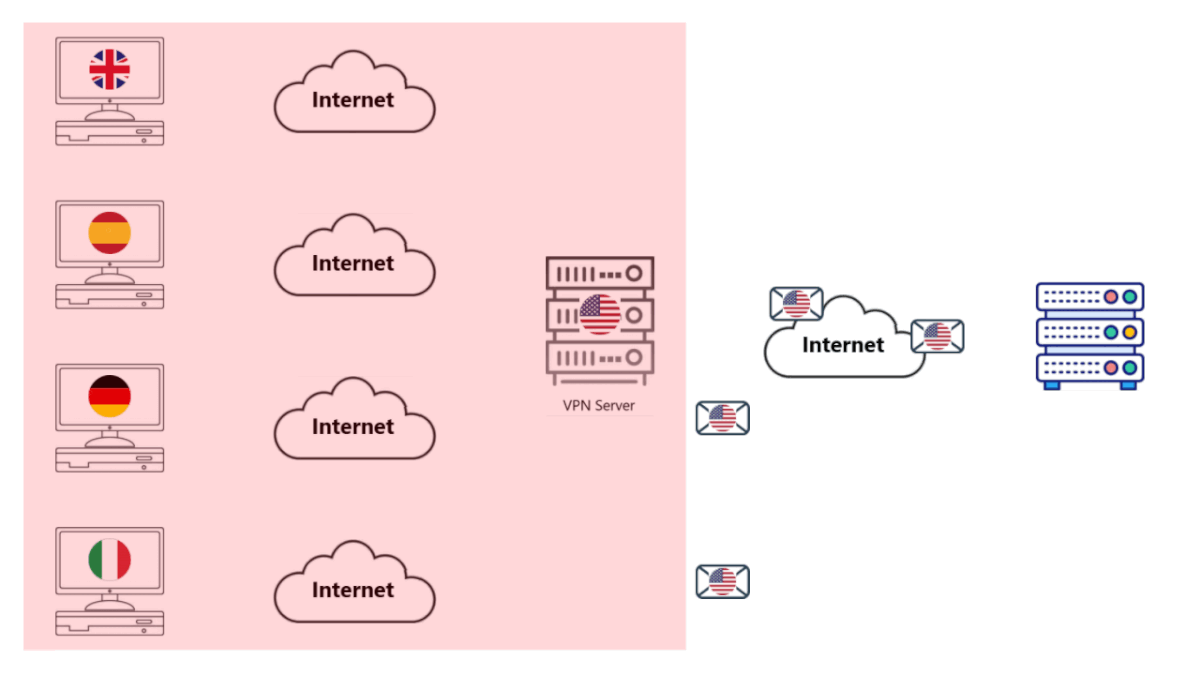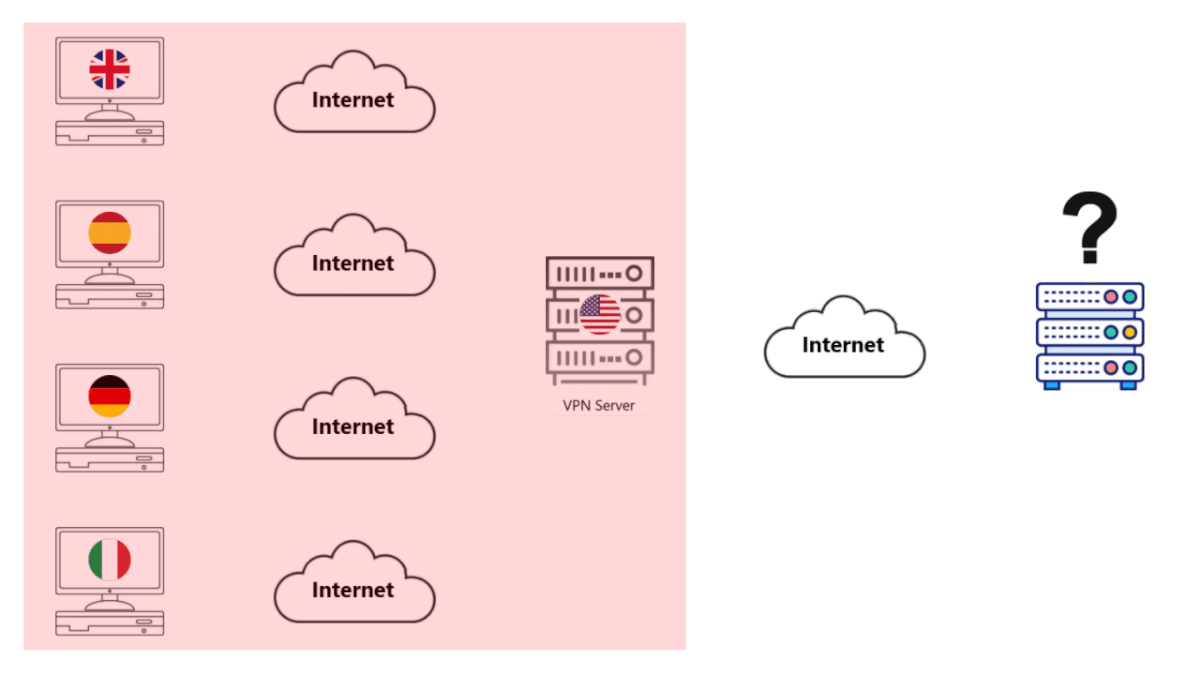 Why is getting a dedicated VPN such a big deal?
Why is getting a dedicated VPN such a big deal?• Covert Bear just wants you to be happy, we won't force you into anything (like the Government or Corporations try to do)
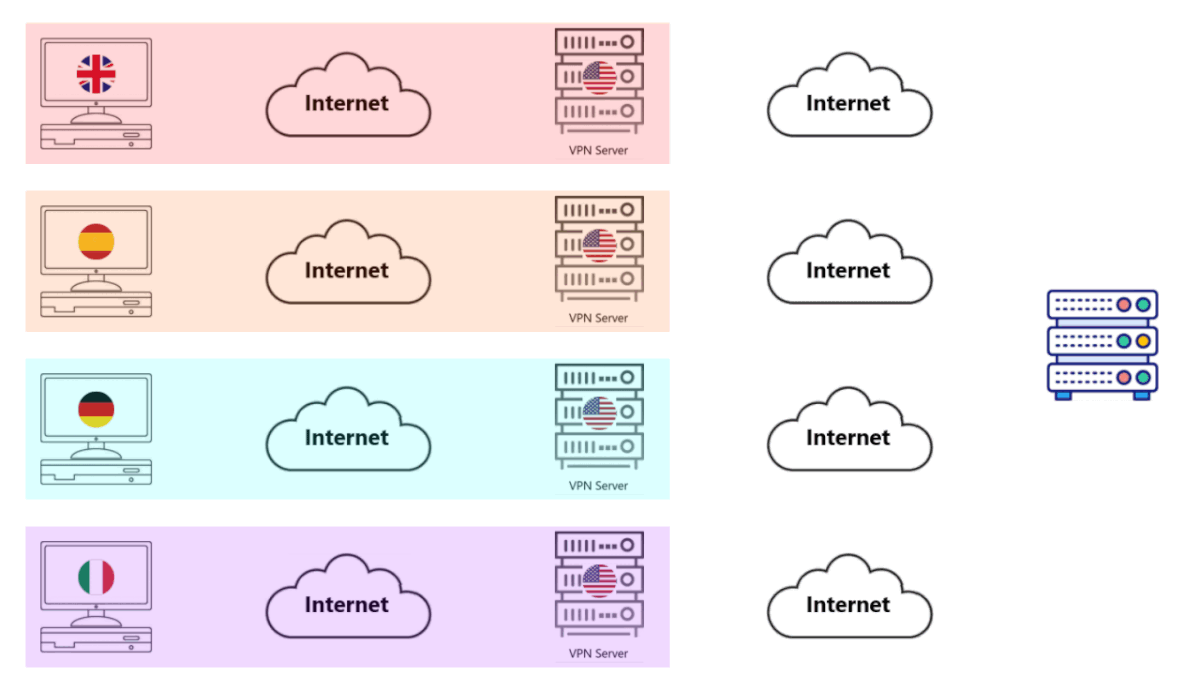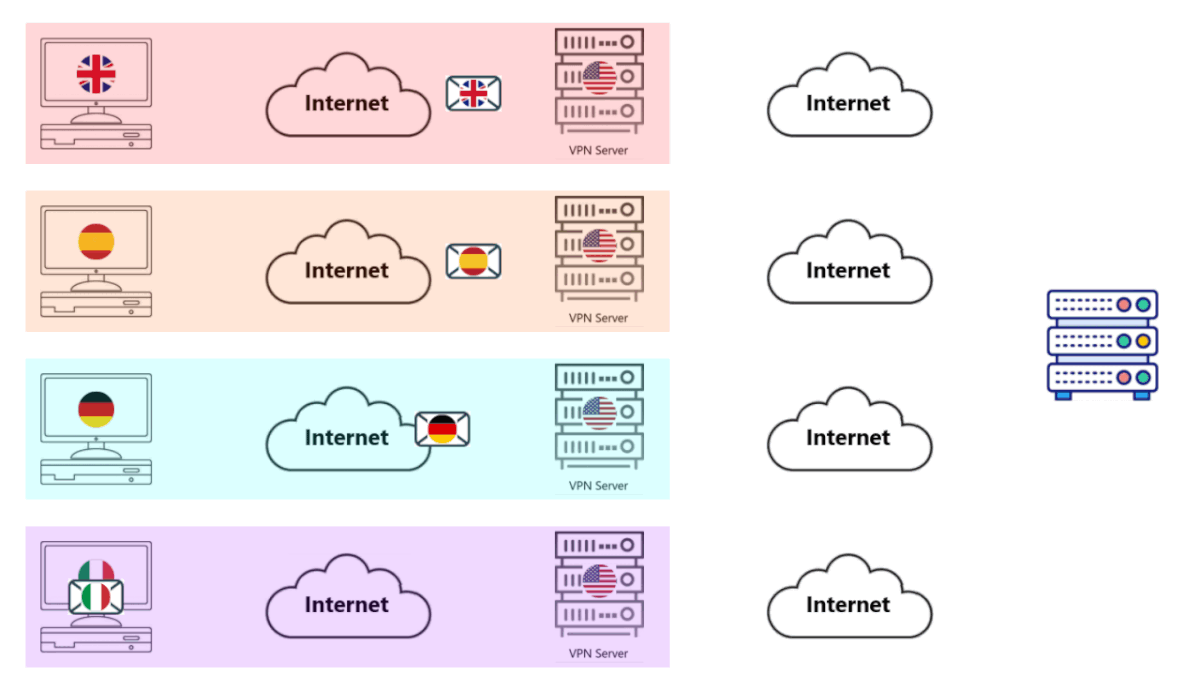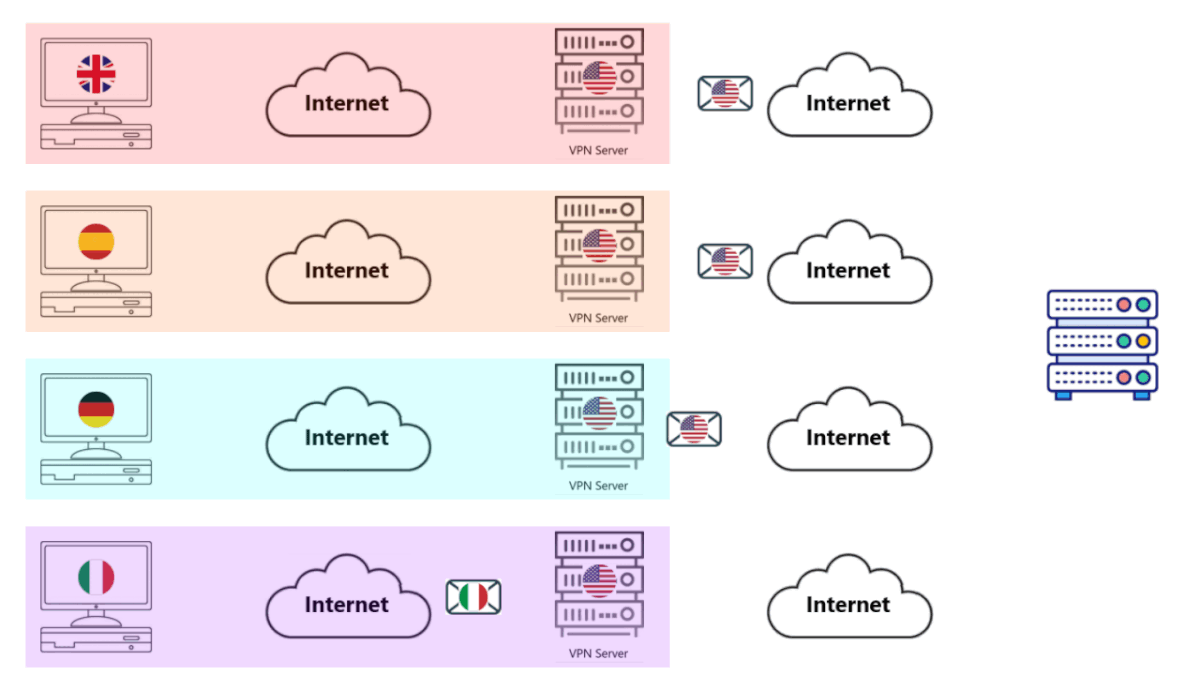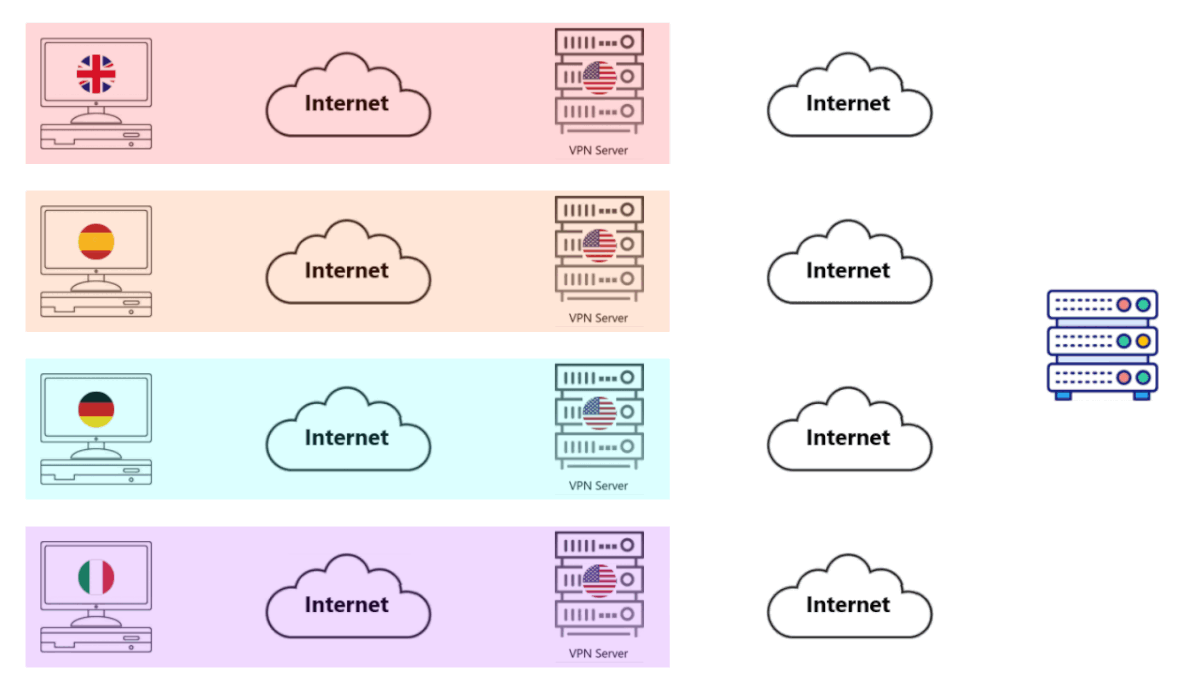
• With Ordinary VPN Servers, you share a Server with everyone else.
• In the image, there are only 3 other computers shown, but in reality there would be thousands if not hundreds of thousands.
• Suppose you try to access a website, such as YouTube or want to buy something on Amazon, or watch a video on Netflix, etc.
• At any given moment, thousands of other people using the same VPN Server may try to access it too.
• All of your computers send your packets to the VPN Server. All of these packets are encrypted and secure.
• The VPN Server decrypts all of these packets and forwards them to the Web Server (for whatever service).
• The Web Server sees thousands (4 in the image, we couldn't make a better GIF yet) of requests from the same Computer.
• That's right, everything in the Red Box above appears to be a single Computer to the Internet.
• The Web Server starts to get nervous, it asks if you're a Robot. You probably know this all too well. You waste precious time trying to prove you're a Human to a Machine.
• In some severe cases, such as with Amazon, your account might get flagged (and the VPN Server definitely gets flagged as being a VPN) because they think one person has 1000+ accounts with them. It might even get blocked.
Why do they flag the VPN Server?
• They make money knowing who you are and what you do, no one wants you to use a VPN.
So how does a Dedicated VPN Server work?
 I see the GIF, how is this any different than an Ordinary VPN?
I see the GIF, how is this any different than an Ordinary VPN?• Imagine the thousands of people from the previous card each have a Dedicated VPN Server (with Covert Bear!)
• Each individual user wants to access some Web Server (of course).
• Each individual computer sends their own packet to their own VPN Server.
• Each VPN Server does what it's supposed to do. It decrypts the packet and sends the request to the Web Server showing itself as the User.
• The Web Server still gets thousands, if not hundreds of thousands, of requests, but this time they are all from different computers. That means it's business as usual, the Web Server does not panic, it accepts and everyone is happy.
• Note, each colored block appears as One Single Computer to the Internet, to the Servers as well.